Recovery-TryHackMe
This is by far the best room for me on THM and I enjoyed it a lot. Hope you will too.
First lets write down what is already given to us:
- A web-server showing some gibberish.
- A web panel to keep track of recovery process at port 1337
- SSH credentials : alex/madeline
- The malware in alex's home directory
Our task is to repair all the damage caused by fixutil and collect flags from web panel running at port 1337. Lets begin.
Run the NMAP first and let see if we can find something else:
nmap -sC -sV 10.10.72.173
Nothing new here. Also run NMAP to scan for all ports to check if we can find something else:
nmap -sC -sV -p- 10.10.157.2
Also run your favorite directory busting tool in the background to check if we can find other interesting web-pages.
Now let us try to SSH to the machine with alex/madeline.
And we are greeted with a series of unending messages and no way to interact with the machine. Well not entirely true. We can still run commands on the system and even chain them like:
ssh alex@10.10.72.173 "uname;whoami;id;pwd;ls -lrta"
And if you get tried of typing password again and again then try this utility - sshpass.
Please read https://linux.die.net/man/1/sshpass before using this utility specially the section "Security Considerations"
sshpass -p "madeline" ssh alex@10.10.72.173 "uname;whoami;id;pwd;ls -lrta"
Install it using the following command:
sudo apt install sshpass
After poking a bit around the .bashrc file in alex's home directory contains the following line:
and this is causing an infinite loop and stopping us to interact via normal SSH. Lets delete this line and try to login via normal SSH.
sshpass -p "madeline" ssh alex@10.10.72.173 "sed -i '$ d' /home/alex/.bashrc"
Keep all the spaces in the command otherwise it will not work.
Check the panel now and it will reveal our Flag 0. Sweet!
But now you will observe that we are kicked out of our SSH session and if you log again in approx 1 min you will be kicked out of SSH again.
Smells like a cron job is running which is doing that. Search for it and ultimately you will find this:
A cronjob name evil is running as root and killing all bash processes every minute. Two things can be done here:
- Lets comment the for loop line /opt/brilliant_script.sh as it is world writable.
- Do privilege escalation to root by adding this line in /opt/brilliant_script.sh - cp /bin/bash /tmp/bash && chmod +s /tmp/bash
Check the control panel again and do refresh. We get our Flag1 now.
And after a minute we get /tmp/bash with suid bit set, which can be used to get root.
We already know that we have fixutil in /home/alex directory. Next step is to analyse what this binary is doing. I first tried to run the "strings" command against it and to my surprise it revealed a lot. Here are few interesting bits out of it:
This bit looked very juicy:
After looking at all the directories and files mentioned above a rough picture starts to emerge about what fixutil might be doing:
- Entry in /home/alex/.bashrc to make it bit difficult for user alex to work the machine via SSH.
- A cronjob /etc/cron.d/evil to kick out users out of the box via script /opt/brilliant_script.sh - which also helped us to get the "root" access.
- Another exe /bin/admin is invoked by fixutil
- Few interesting directories/files:
- /usr/local/apache2/htdocs/
- /opt/.fixutil/
- /opt/.fixutil/backup.txt
- /root/.ssh/authorized_keys
- A user named "security" added with a password.
- A new SSH key added /root/.ssh/authorized_keys
- liblogging.so copied from /lib/x86_64-linux-gnu to /tmp
- /tmp/logging.so moved to directory /lib/x86_64-linux-gnu as oldliblogging.so
- Probably these functions responsible for encrypting web server files - XOREncryptWebFiles, GetWebFiles, XORFile,web_location,encryption_file
Before doing any decompilation and Reverse Engineering, I removed the entry done by fixutil in /root/.ssh/authorized_keys which revealed Flag3:
and also added a password entry for root user in /etc/shadow just in case if I need to login again via SSH. I also removed the entries for the user "security" added by fixutil in /etc/passwd and /etc/shadow which revealed Flag4:
For me till this point it was quite easy and also got a pretty good idea of what is happening, but could add it up all together, so decided to start doing decomposition of fixutil and the admin exe using radare2 which proved to be difficult so I decided to use Ghidra and did this room first so that I know the basics of this tool:- https://tryhackme.com/room/ccghidra
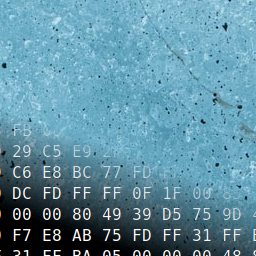
It was pretty easy to use and the outcome was that now I know for sure that the files under /usr/local/apache2/htdocs/ are encrypted using XOR encryption using the key located here:- /opt/.fixutil/backup.txt
XOR encryption is reversible if we know the key, so i searched around and found this code:-
Compiled it and transferred it to the machine by hosting a python server on my local machine and using wget on the target machine. This code will take input and output file name and then ask for the key. Please make sure that you made a backup of /usr/local/apache2/htdocs/ before trying to decrypt as you might do it wrong and then need to restart the room to get it back to current stage. I have done that few times :)
On local machine:
gcc xorencrypt.c -o xorencrypt
python3 -m http.server
On Target machine:
wget http://10.9.6.174:8000/xorencrypt
chmod +x xorencrypt
./xorencrypt /usr/local/apache2/htdocs/todo.html /usr/local/apache2/htdocs/todo.html
Passphrase: AdsipPewFlfkmll
Encrypting /usr/local/apache2/htdocs/todo.html
Encrypted data written to /usr/local/apache2/htdocs/todo.html
./xorencrypt /usr/local/apache2/htdocs/reallyimportant.txt /usr/local/apache2/htdocs/reallyimportant.txt
Passphrase: AdsipPewFlfkmll
Encrypting /usr/local/apache2/htdocs/reallyimportant.txt
Encrypted data written to /usr/local/apache2/htdocs/reallyimportant.txt
./xorencrypt /usr/local/apache2/htdocs/index.html /usr/local/apache2/htdocs/index.html
Passphrase: AdsipPewFlfkmll
Encrypting /usr/local/apache2/htdocs/index.html
Encrypted data written to /usr/local/apache2/htdocs/index.html
Now check the control portal and the main web-page we got out Flag5:
The gibberish text is gone and we are very close now.
Lets remove/restore the other files which we already know:
mv /lib/x86_64-linux-gnu/liblogging.so /tmp/
mv /lib/x86_64-linux-gnu/oldliblogging.so /lib/x86_64-linux-gnu/liblogging.so
I must say that the last step took a lot of time for me as I kept deleting oldliblogging.so along with other files which we discovered (created by the malware) instead oldliblogging.so needed to be restored to liblogging.so to get the Flag2.
Big applauds to the room creator as this room was full of knowledge and fun.


Comments
Post a Comment