Simple CTF write-up - TryHackMe
Recently I tried to solve the Simple CTF room from https://tryhackme.com and found out few interesting things.
I was able to root the box, but without using the normal SQL injection method which I discovered later by reading more about this room.
1. First step (as always :)) use NMAP to find out what is running on the box:
1. First step (as always :)) use NMAP to find out what is running on the box:
Ok, so the following ports are open among top 1000 ports:
2. Login FTP using Anonymous:
| Port | Service Name | Notes |
|---|---|---|
| 21 | FTP | Anonymous login allowed |
| 80 | HTTP | robots.txt |
| 2222 | SSH | Non standard ssh port |
2. Login FTP using Anonymous:
As
you can see there seems to be a user named - “Mitch” and the notes
above indicates that user mitch have got a weak password - Time for
Brute Forcing.
3. Brute force SSH for user mitch:
hydra -s 2222 -v -q -l mitch -P /usr/share/wordlists/rockyou.txt -e nsr -t 4 -w 5 10.10.67.56 ssh
Hydra was able to crack the password very quickly
4. Get the user flag:
SSH with user mitch and the cracked password and get the user flag:
4. Get the user flag:
SSH with user mitch and the cracked password and get the user flag:
5. Privilege escalation to get root flag:
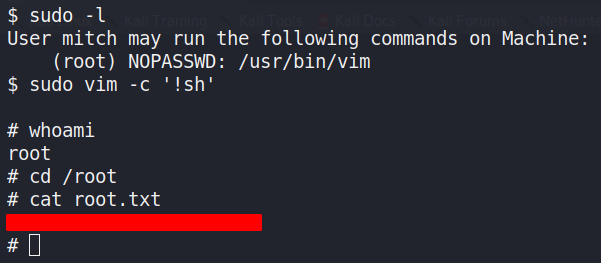
Now to get the root flag, lets first check what is this allowed run as sudo using ‘sudo -l’
Now to get the root flag, lets first check what is this allowed run as sudo using ‘sudo -l’
Ah, vim can be run as sudo and without password. Now use your favorite resource like gtfobin or use my notes from this post:
https://basicpentesting.blogspot.com/2020/06/70-ways-to-get-root-linux-privilege.html to get root shell and then root flag:
All done !
In my other post, I will do a write of exploiting this machine using the CVE-2019-xxxx








Great instruction
ReplyDeleteThanks..
DeleteBrother, thank you. I was stuck on the Privesc part, I thought about giving a find / -perm 777 /dev/null>2& however it did not work, Thanks
ReplyDelete